Malware discovered in the Stratfor email file dump provided by Wikileaks is not limited to torrents - curated content on the Wikileaks website also infected
Several months ago I identified malicious software contained within a torrent available for download from Wikileaks. The torrent was the most recent and most complete copy of what Wikileaks titled the "Global Intelligence Files" - a large trove of emails and attachments from defense contractor Stratfor. The story as it is widely understood is that former Lulzsec member and hacktivist Jeremy Hammond was involved in the acquisition of these files from Stratfor and provided them to Wikileaks. Among the many files included in the leak I have identified 18 that have malicious software; most of those are embedded within PDF and DOC files. Some of the attacks I discovered are old, others are less old. Only two of the 18 files are blocked from downloading using Google Chrome's malware protection service, for example. In a second post, I decompile one of these two (older) files using PE Explorer and Hex-Rays IDA to demonstrate how the file corrupts the Microsoft Connection Manager while posing as an application called iPassConnect in order to faciliate infection with a Magistr worm variant.
Since that time I have made numerous attempts to contact Wikileaks so that they could inform their users that the torrent contained malicious software. After receiving no response, I began to publicize my findings by posting them on Hacker News/Ycombinator and similar sites like Slashdot and Reddit. My post on Hacker News quickly reached the front page and attracted the attention of the former leader of Lulzsec, Hector Monsegur (aka sabu), who confirmed the validity and importance of my findings in a series of public tweets.
In my original post, I speculated that:
The file name of each torrent contains the date of its publication. Meanwhile, the number to the far right, beginning with 1603, indicates the size of the torrent in bytes. While the relationship between the size of a torrent and the size of the files it contains is not a direct one in all cases, in this case it is a fairly direct relationship because we are dealing with large lists of small files. The last torrent, which I have identified as containing malware, has a size of 121071 bytes. The point here is that you can see that the number of files contained in the archive grows over time.
The torrent file that contains malware is the only file in the directory with a nomenclature that does not include a full date (it was also created using bzip instead of 7zip); the filename is simply gifiles-2014.tar.bz2.torrent. Initially, this meant I was not sure of the exact date that the torrent was released.
I knew that the relatively small number of curated content was available on the Wikileaks.org website. Today I was able to confirm that malicious files and their related attachments are also being hosted on Wikileaks.org, as individual uncompressed files. I have composed a list of these files, their URLs and basic file information on pastebin: (I have embedded the pastebin below as an iframe; if you don't trust iframes in your browser you can click through the prior link instead)
NOTE: Wikileaks has multiple URLs servicing multiple directory structures, all that eventually seem to point to the same place. So for example, https://wikileaks.org/gifiles/docs/35/3547802_plans-coordinates-and-executes-.html and https://search.wikileaks.org/gifiles/emailid/3547802 both point to the same content (and include the same malware attachment available for download).
While I am not alone in my concern over the circulation of an infected torrent of the nature I described in my first post, posting individual infected files directly to *.wikileaks.org domain and several subdomains in a curated manner is likely more dangerous - users are more likely to consider the following a link to content that has in some fashion been secured:
An expectation that a video posted on Fox News will not contain an embedded script is not a wild expectation. Similarly a New York Times article that includes a photo in an article is usually believed to not contain spyware. This is a basic expectation of service on every website, not just news outlets. Primary sources are important. User transparency is also important.
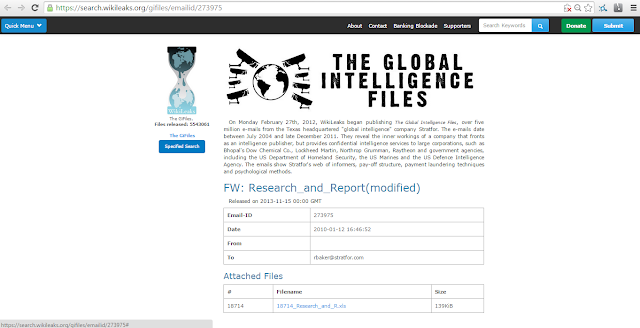
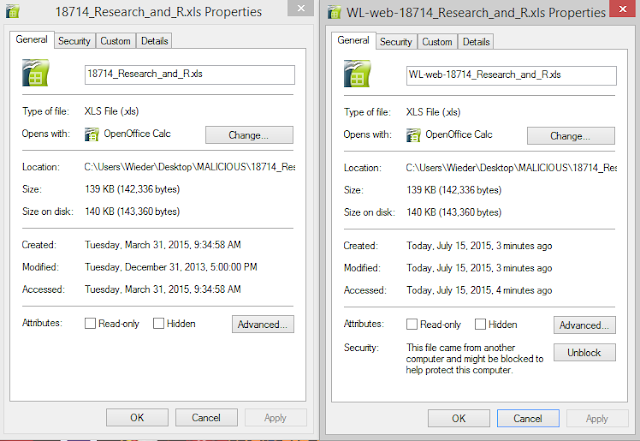
The attached file above, "18714_Research_and_R.xls", appears to be a normal Excel spreadsheet but in fact contains an embedded OLE. It is the exact size in bytes as the same attachment I discovered within the torrent that started this series of posts:
Of course there is no need to take my word for it. The file contains an embedded OLE and PE file - the hallmarks of malware designed to exploit vulnerabilities in the Microsoft Office Suit. Of note are the following:
As I mentioned earlier in this post, Google malware service in Chrome detects only three of the so far 18 infected attachments. The two that are detected are the two oldest malware by the date sent and are both compressed executables (one a .COM and the other two are .EXE) rather than embedded within documents. Here is what downloading one of these off of the Wikileaks website looks like as of now:
Both of the old nasty .EXE's appear to have been sent from mfriedman@stratfor.com, which as far as I can tell, was/is the email address of Meredith Friedman, the VP of Communications for Stratfor:
Would anyone care to bet me a dollar that in late 2003 her email password was "mfriedman", her birthday, "12345" or some combination thereof?
The source of the .COM file is as follows:
Finally for today, please do not make the mistake of assuming that all of the exploits are from this time period and thus are of no important to modern computer users. I cannot make this clear enough: these two files are the *oldest* of the malicious files I have discovered.
To return to the first post in our series on the Wikileaks / Strafor email malware click here.
If you are looking for the second post, where we look briefly inside one of the executables click here.
This is the link for my conversation with Hector Monsegur AKA sabu of Lulzsec on the Wikileaks / Strafor email malware.
Since that time I have made numerous attempts to contact Wikileaks so that they could inform their users that the torrent contained malicious software. After receiving no response, I began to publicize my findings by posting them on Hacker News/Ycombinator and similar sites like Slashdot and Reddit. My post on Hacker News quickly reached the front page and attracted the attention of the former leader of Lulzsec, Hector Monsegur (aka sabu), who confirmed the validity and importance of my findings in a series of public tweets.
In my original post, I speculated that:
"The data is indeed massive, over 5.5 million emails. Perhaps so massive that ~ two years was not long enough to properly review and sanitize these files prior to their complete publication in 2014 (from the time they were received by WL sometime around 2012)."The publication of the Global Intelligence Files by Wikileaks began on February 27th, 2012. The entire email server spool was not dumped onto the internet at one time. The publication was curated, with only a small percentage of the emails being published initially. Over time, more emails were published. This progression can be easily viewed on the directory hosting the torrents for the Stratfor leaks:
The file name of each torrent contains the date of its publication. Meanwhile, the number to the far right, beginning with 1603, indicates the size of the torrent in bytes. While the relationship between the size of a torrent and the size of the files it contains is not a direct one in all cases, in this case it is a fairly direct relationship because we are dealing with large lists of small files. The last torrent, which I have identified as containing malware, has a size of 121071 bytes. The point here is that you can see that the number of files contained in the archive grows over time.
The torrent file that contains malware is the only file in the directory with a nomenclature that does not include a full date (it was also created using bzip instead of 7zip); the filename is simply gifiles-2014.tar.bz2.torrent. Initially, this meant I was not sure of the exact date that the torrent was released.
I knew that the relatively small number of curated content was available on the Wikileaks.org website. Today I was able to confirm that malicious files and their related attachments are also being hosted on Wikileaks.org, as individual uncompressed files. I have composed a list of these files, their URLs and basic file information on pastebin: (I have embedded the pastebin below as an iframe; if you don't trust iframes in your browser you can click through the prior link instead)
NOTE: Wikileaks has multiple URLs servicing multiple directory structures, all that eventually seem to point to the same place. So for example, https://wikileaks.org/gifiles/docs/35/3547802_plans-coordinates-and-executes-.html and https://search.wikileaks.org/gifiles/emailid/3547802 both point to the same content (and include the same malware attachment available for download).
While I am not alone in my concern over the circulation of an infected torrent of the nature I described in my first post, posting individual infected files directly to *.wikileaks.org domain and several subdomains in a curated manner is likely more dangerous - users are more likely to consider the following a link to content that has in some fashion been secured:
An expectation that a video posted on Fox News will not contain an embedded script is not a wild expectation. Similarly a New York Times article that includes a photo in an article is usually believed to not contain spyware. This is a basic expectation of service on every website, not just news outlets. Primary sources are important. User transparency is also important.
The attached file above, "18714_Research_and_R.xls", appears to be a normal Excel spreadsheet but in fact contains an embedded OLE. It is the exact size in bytes as the same attachment I discovered within the torrent that started this series of posts:
Of course there is no need to take my word for it. The file contains an embedded OLE and PE file - the hallmarks of malware designed to exploit vulnerabilities in the Microsoft Office Suit. Of note are the following:
An API-Hashing signature is stored at 0x3ad1 There are two decryption loops at 0x00003932 and 0x00003934 The embedded OLE signature is stored at 0x7a00 A XOR encrypted MZ/PE signature is stored at 0x5a00 and the encryption key is 0x97 A ROL encrypted OLE signature is stored at 0x7a00 and the encryption key is 0x08OfficeMalScanner can duplicate these results. When I ran OfficeMalScanner against "18714_Research_and_R.xls" using the brute debug scan mode, the scan produced a malicious index of 62. Several antiviruses will detect this file. Depending on which you use, it might declare the file to use CVE-2009-3129 or CVE-2009-0557 (it probably relies on both exploits at different points). I have created bin files from memory dumps of the embedded OLE and PE (as I have for the roughly dozen similar malware payloads); I am happy to provide those to interested researchers. Here are the relevant signatures:
MD5 2746a014bdd9f7bf252262b82cf63e11 SHA1 cf525700b9e1027c4628fa9689bf68777291c60d SHA256 4f9550c3f3abbfac4153b4467666e7a46e29ab974627ffd7feed7a711d55ffcd
As I mentioned earlier in this post, Google malware service in Chrome detects only three of the so far 18 infected attachments. The two that are detected are the two oldest malware by the date sent and are both compressed executables (one a .COM and the other two are .EXE) rather than embedded within documents. Here is what downloading one of these off of the Wikileaks website looks like as of now:
Both of the old nasty .EXE's appear to have been sent from mfriedman@stratfor.com, which as far as I can tell, was/is the email address of Meredith Friedman, the VP of Communications for Stratfor:
Email-ID 3451016 Date 2003-11-04 15:32:57 From mfriedman@stratfor.com To mooney@stratfor.com, wit@stratfor.com Subject: FW: Re[2]: our private photos bkarngkr Email-ID 3491917 Date 2004-01-27 01:03:10 From mfriedman@stratfor.com To mooney@stratfor.com Subject: FW: HI
Would anyone care to bet me a dollar that in late 2003 her email password was "mfriedman", her birthday, "12345" or some combination thereof?
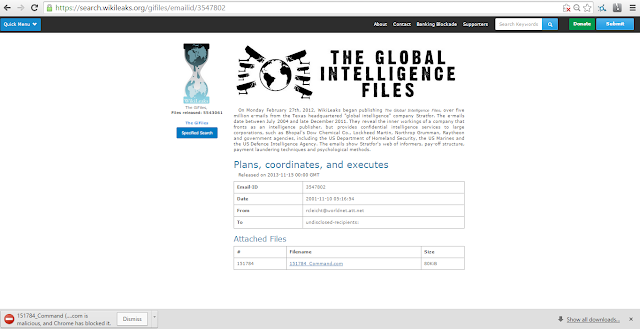
The source of the .COM file is as follows:
Email-ID 3547802 Date 2001-11-10 05:16:54 From rcleicht@worldnet.att.net To undisclosed-recipients: Subject: Plans, coordinates, and executes
Finally for today, please do not make the mistake of assuming that all of the exploits are from this time period and thus are of no important to modern computer users. I cannot make this clear enough: these two files are the *oldest* of the malicious files I have discovered.
To return to the first post in our series on the Wikileaks / Strafor email malware click here.
If you are looking for the second post, where we look briefly inside one of the executables click here.
This is the link for my conversation with Hector Monsegur AKA sabu of Lulzsec on the Wikileaks / Strafor email malware.